A single data breach can cost your organization an average of $1.3 million in lost business! Yet, many vulnerabilities go unnoticed – until it’s too late. It takes about 194 days on average to find a breach. You can’t protect what you can’t see, can you? This is where a rigid DevSecOps security framework can help save your bucks as well as your systems.
This blog outlines the best practices for implementing DevSecOps effectively, enabling organizations to innovate fast without compromising on security.
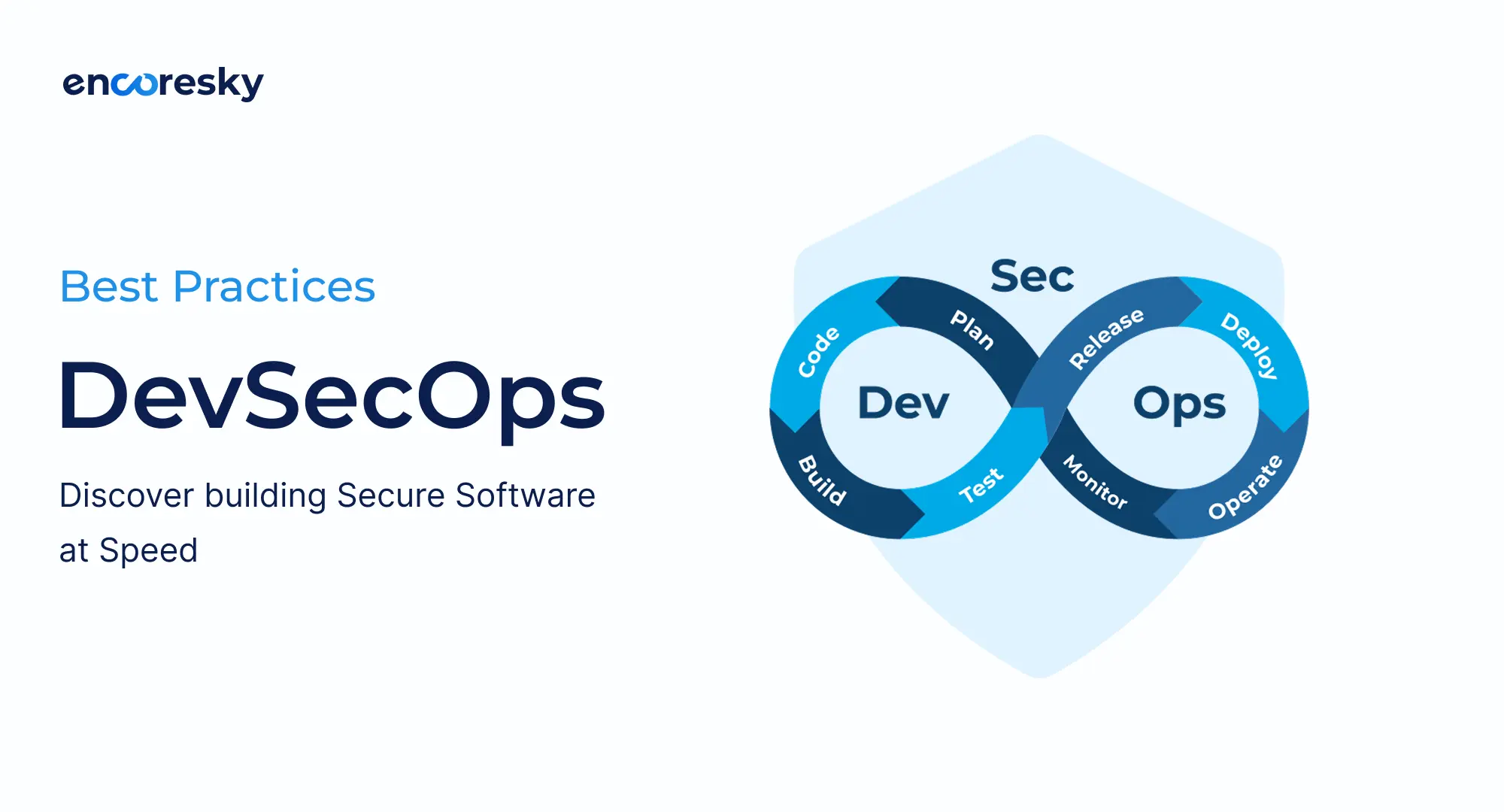
10 Best Practices for DevSecOps Security in 2025
1. Automate security at every stage
- Manual security reviews create missed vulnerabilities and delayed releases.
- Automating security tasks such as vulnerability scanning, and compliance checks can minimize risks.
- Consider using tools that integrate with CI/CD pipelines.
2. Shift security left to catch issues early
- Shifting security left means integrating security practices at the coding level.
- Developers should run security tests and apply secure coding standards from the start.
- Adopting secure coding practices can reduce post-release security incidents.
Pro-tip: Consider implementing SAST (static application security testing) tools directly into the developer’s IDE. This will help identify vulnerabilities before they arise.
3. Threat modeling to identify high-risk areas
- Threat modeling helps visualize and mitigate potential attack vectors.
- Identifying high-risk components and weak points in the system can help prioritize security controls effectively in industries such as healthcare, FinTech, etc.,
Pro-tip: Tools like the Microsoft Threat Modeling Tool shall help assess and refine security controls during the design phase.
4. The Use of Artificial Intelligence in Security for DevSecOps
- With the use of AI algorithms, security postures are advanced through data anomaly detection.
- Real-time action is linked to automated threat response, which tailors in prioritization of risks.
- The addition of AI security tools assists in boosting visibility of threats.
5. Policy as Code (PAC) Provides a Uniform Benchmark for Security Policies
- Policy as Code (PaC) is responsible for programmably defining and enforcing set security policies.
- Consistency within the practices is achieved alongside a reduction in configuration drifts.
- Security stipulations within the cloud infrastructure, APIs, and Kubernetes can be enforced through the use of OPA.
6. Use Role Based Access Control and Disclosure Minimization
- The chances of becoming victims of insider malicious acts, cybersecurity.
- Access to a computer system is controlled and administered through positions in the organization which is referred to as (RBAC).
7. Placed on Continuous Surveillance and Ready to Take Care of Possible Events
- There must be an active tracking process after deployment to avoid activities that look suspicious, to breach the system.
- The extent of damage to security can be reduced by ready incident response plans.
8. Assure your success by preparing best DevSecOps tools for 2025
Implement new AI-based DevSecOps tools which would offer the best security with low interference in existing workflows.
- Automated enforcement of policy and security protocols to security and compliance
- Vastly accessible due to low-code or no-code automation
- Vulnerability scanning is done in real-time
- Alignment with three fundamental components of DevSecOps which are prevent, resolve and secure.
‘9. Security-First’ culture across teams
- Your system can’t be protected by DevSecOps alone.
- The “security-first” culture helps define the role of stakeholder, developers, security personnel or the operations in efficiently securing applications.
- Train regularly on security and conduct workshops for your team.
10. Compliance with industry standards
- Using industry policies such as effective data protection frameworks enhance trust from customers.
- Carefully define standards related to HIPAA, PCI-DSS and GDPR.
- With automation, enforcing compliance can be consistently maintained.
Conclusion
DevSecOps is more than just server or cloud configuration— it’s a necessary evolution of modern software development. By weaving security into the fabric of DevOps, organizations can deliver faster without sacrificing safety. These best practices offer a blueprint for integrating security holistically, building trust in every release.
Whether you’re starting from scratch or enhancing your current setup, remember: DevSecOps is a journey, not a destination. Keep automating, keep learning, and keep securing. Connect with us today.